Introduction to the Deep Web and its Role in Privacy
The Deep Web is often shrouded in mystery and intrigue. While many associate it with hidden treasures or illicit activities, its true impact on privacy is profound and multifaceted. In this vast digital underworld, anonymity reigns supreme, making it both a sanctuary for the cautious and a playground for those with nefarious intentions.
As users navigate this shadowy realm, tools like Bidencash.cc, Bins, and DOB have emerged as significant players. These resources offer an enticing yet troubling glimpse into how personal information can be manipulated or compromised. Understanding their rise sheds light not just on privacy concerns but also on the broader implications of our online behaviors.
Join us as we delve deeper into these elements of the Deep Web that shape our understanding of privacy today. What are the risks? How do people exploit these tools? And most importantly, what can you do to protect yourself in this unpredictable landscape? Let’s explore together.
The Rise of Bidencash CC, Bins, and DOB
In recent years, the digital underground has witnessed an alarming surge in tools like Bidencash CC, bins, and date of birth (DOB) lists. These elements have become staples for those navigating the murky waters of online fraud.
Bidencash CC specifically refers to stolen credit card information tied to the name “Biden.” This clever naming plays on current events and gives it a certain allure among cybercriminals. The anonymity offered by these transactions is enticing; users believe they can bypass traditional banking safeguards.
Bins serve as another crucial component. They are bank identification numbers that help scammers validate cards before making purchases or reselling them. When combined with DOB data, criminals gain access to personal details necessary for identity theft.
This combination creates a perfect storm for those looking to exploit unsuspecting victims without much risk of being caught.
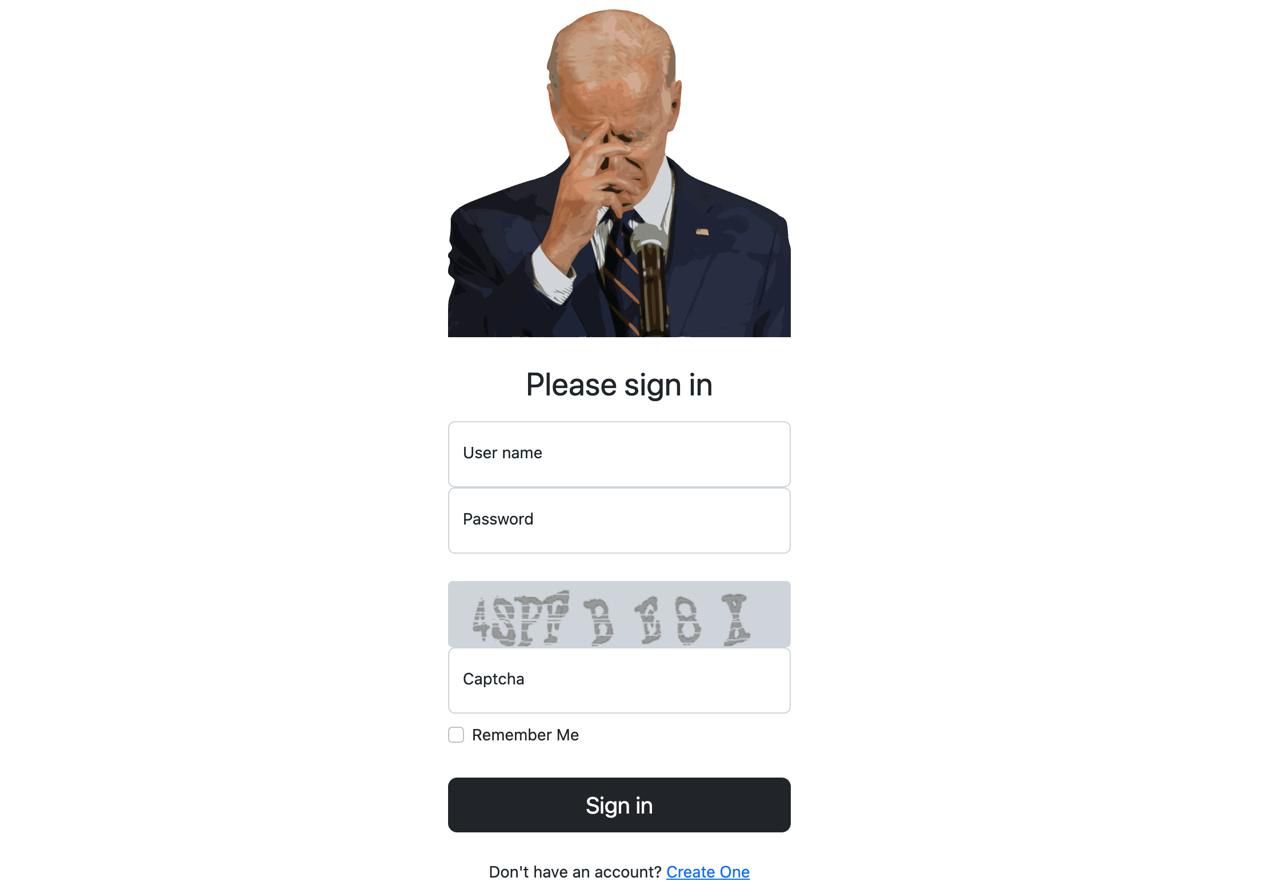
A Screenshot of Bidencash (bidenscash.cc) login page
How These Tools are Used for Fraud and Identity Theft
Bidencash login, along with bins and DOBs (Date of Birth), has become a notorious trio in the world of online fraud. Scammers leverage these tools to impersonate individuals and commit identity theft seamlessly.
Using stolen credit card data, criminals can make unauthorized purchases or sell goods on various platforms. Bins provide access to specific bank information, allowing hackers to exploit weaknesses in payment systems.
DOBs add another layer of deception. They trick verification processes that rely on personal data authentication. This makes it easier for fraudsters to open accounts under someone else’s name without raising red flags.
The anonymity offered by deep web transactions fuels this criminal ecosystem. As long as these tools exist, the risk of becoming a victim remains high for many unsuspecting users navigating the internet.
Related: Jokerstash
The Dark Side of the Deep Web: Illegal Activities
The deep web is often shrouded in mystery, but its dark side reveals a troubling reality. Here, anonymity fosters illegal activities that thrive away from the prying eyes of law enforcement.
Markets selling drugs, weapons, and stolen data operate with relative impunity. Transactions occur using cryptocurrencies, making them hard to trace. This environment attracts individuals looking to exploit vulnerabilities for personal gain.
Moreover, hacking services are readily available for hire. From identity theft to corporate espionage, these illicit offerings have dire consequences for victims.
Scams also flourish in this hidden realm. Fake websites and counterfeit goods entice unsuspecting users who believe they’re safe behind their screens.
As awareness grows around these dangers, navigating the deep web becomes increasingly complex for those seeking privacy or alternative resources without falling prey to its darker aspects.
Protecting Your Privacy on the Deep Web
Navigating the Deep Web can feel like wandering through a digital labyrinth. Privacy is paramount, especially when engaging with sensitive information.
To bolster your privacy, consider using a reliable VPN. This masks your IP address and adds an extra layer of security. It’s crucial for obfuscating your online activities from prying eyes.
Utilizing anonymous browsers like Tor can also enhance your protection. These tools help you access hidden sites while keeping your identity concealed.
Be cautious about sharing personal data. Many people underestimate how easily seemingly harmless details can be exploited.
Regularly update passwords and utilize strong, unique combinations for each site. Consider password managers to keep track securely.
Educate yourself on the latest threats in the digital landscape. Awareness is one of the best defenses against potential breaches on the Deep Web.
Alternative Methods for Online Transactions
As the landscape of online transactions evolves, people are exploring safer and more private alternatives. Cryptocurrencies like Bitcoin and Ethereum provide a level of anonymity that traditional payment methods lack.
Digital wallets also offer secure ways to store and transfer money without revealing personal information. Services such as PayPal or Venmo allow users to conduct transactions while minimizing exposure.
For those seeking extra privacy, prepaid cards can be an excellent option. They enable purchases without linking directly to bank accounts or personal data.
Moreover, blockchain technology is gaining traction for its transparent but secure nature. It eliminates intermediaries, letting users maintain control over their funds.
Exploring these alternative methods helps safeguard your financial identity in an increasingly digital world. Each option presents unique benefits tailored for different needs, ensuring there’s something for everyone navigating the realm of online payments.
The Future of Deep Web Technology and Its Impact on Privacy
The landscape of the Deep Web is always evolving. Technologies like Bidencash cc, along with tools such as bins and DOBs, are becoming more sophisticated. This evolution raises questions about privacy and security.
As these tools gain traction, they challenge traditional concepts of anonymity online. While some users may leverage them for legitimate reasons, many exploit them for fraudulent activities. The dual nature of this technology creates a complex web where privacy can be both safeguarded and violated.
Looking ahead, it’s clear that regulation will play an essential role in shaping the future of Deep Web technologies. Striking a balance between user privacy and preventing crime presents ongoing challenges for authorities worldwide. As new solutions emerge to protect personal data online, users must stay informed about their options.
Those who navigate this digital underworld should remain vigilant. Understanding how tools like Bidencash.cc operate not only helps in maintaining one’s own security but also highlights the broader implications for society at large when it comes to online safety and privacy rights.
It’s an intricate dance between innovation and caution—one that will define our interactions on the internet in years to come.

